Security Scanner and Monitor User Guide
Introduction

- Welcome to Website Security SCANNER and MONITOR by H-X Technologies! These professional automated services are designed for the protection of your websites. This guide will help you to use our services in the best possible way, even if you are not a cybersecurity specialist.
- First, if you have not read the Frequently Asked Questions page, we suggest you do that because it contains some important initial information about information security assessment and information security vulnerabilities, also known as technical vulnerabilities. Then you can look through the Wikipedia page about computer vulnerabilities. This knowledge will help you to use our services optimally, however, they are also designed for beginners.
- Website security vulnerabilities can be present in the source code or configuration of your web pages, web server, web applications, databases, database engines, backend application, etc. Your website can have security vulnerabilities, even if nobody knows about that yet. It is always better when the provider of your website components or the security researchers find the vulnerabilities before the hackers do (Darknet, black market, etc.). However, sooner or later, any vulnerability becomes known to the security researchers. That can happen both before and after hackers exploit it in their attacks. The security researchers update special vulnerability databases, knowledge bases, security scanners, and scanning engines as soon as possible, to help us uncover whether your websites are vulnerable or not.
- Our Website Security SCANNER and MONITOR use several vulnerability databases and scanning engines to help better detect various website vulnerabilities. Some of the engines: Nikto, SSLscan, DNS Bruteforcer, DNS Zone Transfer analyzer, DNS Harvester, Robots.txt Analyzer, Bruteforce predictables discovery, Sqlmap, Wpscan, Joomscan, OWASP ZAP (Zed Attack Proxy, zaproxy). You do not have to install these engines on your computer, configure, schedule or run them manually. We do this for you. Moreover, we continuously monitor the security of your website and notify you, when its vulnerabilities increase or decrease. Now let us see how to use these services.
How to use the Website Security Scanner
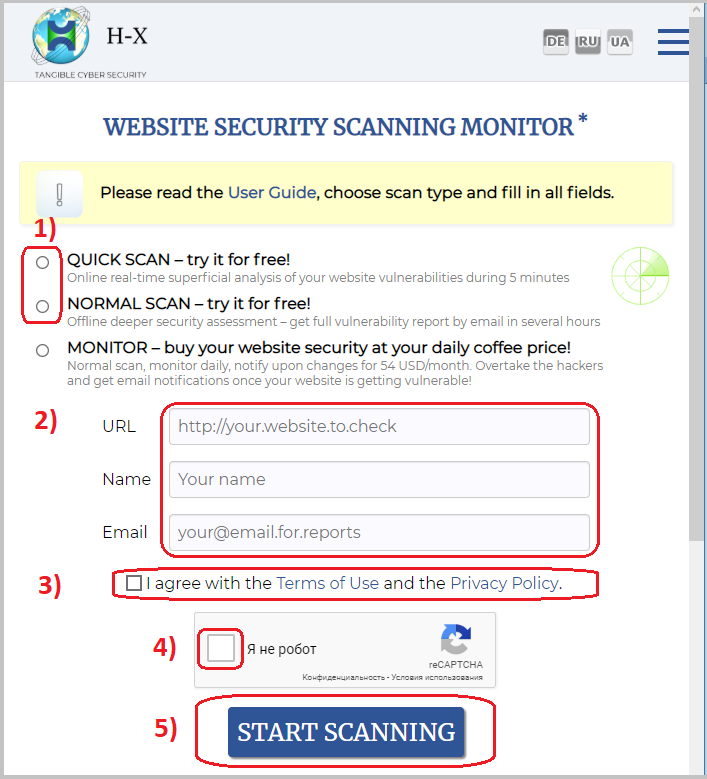
- WEBSITE SECURITY SCANNER (Vulnerability Scanner) provides a free on-demand automatic analysis of your website.
- In short, just go to the Scanner Home, 1) select QUICK SCAN or NORMAL SCAN, 2) paste your website URL (address), type your name and email, 3) click the checkbox that you agree with the Terms of use and the Privacy Policy, 4) check the ‘I'm not a robot’ (CAPTCHA) checkbox, 5) click the ‘Start scanning’ button and follow the instructions.
- What is the difference between the QUICK SCAN and NORMAL SCAN? The Quick Scan only takes 5 minutes, does not need email confirmation, but gives very limited and less reliable results. The Normal Scan requires you to read an activation email notification and click the activation link in it. The Normal Scan can take several minutes or even hours, but gives more results, including a convenient report.
- Why do you need to notify your website hosting service provider about the vulnerability scanning? Sometimes the providers block vulnerability scanning attempts. Of course, it is good for you, because the provider will probably block a hacker's attempts as well. However, what if hackers use more sophisticated methods to circumvent the provider's security controls? Never rely on a single security layer! Your website should be secure itself, independently from any provider.
Therefore, we recommend making an exclusion for our scanner in the provider security controls like WAF or IPS, to get more objective information about the security of your website itself, and not the security of your hosting provider.
Another reason to notify the provider about the vulnerability scanning is that sometimes, although very rarely, they may consider the scanning a real attack and report it. According to our Terms of use, the users take responsibility for the vulnerability scanning, not us. Therefore, if we receive any complaints, we will have to redirect them to the user who started the scanning. - Since we send many activation emails, reports and notifications to users' mailboxes, sometimes these emails fall into the spam folder. You should always check your spam box for our messages so as not to miss them. You can use the ‘Not Spam’ or a similar button to prevent further false spam filtering.
-
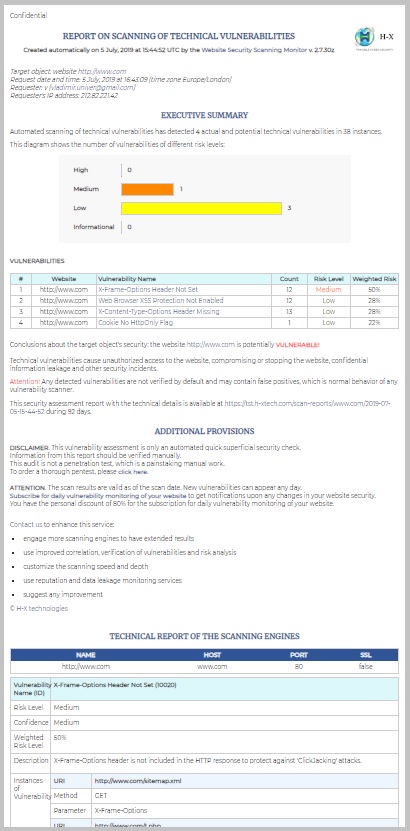 What if you receive our Scanning Report stating that your website is potentially VULNERABLE? Well, don't panic! Not every vulnerability is exploitable or dangerous. You should show the report to your information security analyst, or at least to your technical support to verify and evaluate the vulnerabilities. It is very common for all vulnerability scanners to give false positives. We always insist that any scanning results should be verified manually, and we will be happy to help you.
What if you receive our Scanning Report stating that your website is potentially VULNERABLE? Well, don't panic! Not every vulnerability is exploitable or dangerous. You should show the report to your information security analyst, or at least to your technical support to verify and evaluate the vulnerabilities. It is very common for all vulnerability scanners to give false positives. We always insist that any scanning results should be verified manually, and we will be happy to help you.
- What if the Report states that your website is potentially PROTECTED? Well, do not relax! There is no omniscient vulnerability scanner, and never will be. However, our scanning engines are constantly learning. Try to scan later, and you may get different results. Tired of having to start the scanning manually? Then you need our Vulnerability Monitoring Service described below.
How to use the Website Security Monitor
- WEBSITE SECURITY SCANNING MONITOR is a useful subscription service, which uses the Security Scanner engines to perform daily scanning sessions, tracks your website vulnerabilities over time, and notifies you when vulnerabilities have increased, decreased or changed. Since the Monitor is based on the Scanner, you can use the above instructions and your experience with the Scanner while working with the Monitor. Namely, form filling, notifying your hosting provider, spam folder checks, report handling, etc.
- To use the SECURITY MONITOR, go to the Scanner and Monitor Home, fill in the form just like for the Scanner, but click the ‘MONITOR’ radio button. The ‘Period’ drop-down menu will appear so that you could select the needed monitoring timespan – one to several months. After clicking the ‘Start scanning’ button, you will receive an activation email notification. Please notify your website hosting provider about the vulnerability scanning, and click the activation link to go to the subscription payment page.
- On the subscription payment page, you will see the information about the subscription parameters, price, etc. and an invitation to continue the payment process. All payments are processed by a professional processing center, therefore we do not have any access to your card data. Immediately after a successful payment, the monitoring is activated, and the first scanning session is queued.
- In the activation notification email, you will get information about your subscription and a link to your monitoring dashboard.
- Do not forward this email to anyone and keep all our messages and notifications confidential This will prevent unauthorized persons from accessing your dashboard and information about vulnerabilities.
- After the first scanning session is completed, you will receive a report with information about the current security status of your website. This report is very similar to the usual SCANNER report described above. As with any vulnerability assessment report, the Monitoring reports may contain false positives.
- One of the features of our MONITOR is that notifications will not be sent if there are no changes to your website vulnerabilities. For example, if you analyzed the report once and decided that some of the findings are false positives, you will get a new monitoring notification, only when new vulnerabilities appear, or existing vulnerabilities disappear. However, you can open your daily monitoring reports from the monitoring dashboard whenever you want within the retention period.
- Please note that when your website or its components are temporarily or partially unavailable to our scanning engines, less information about vulnerabilities may be obtained, so a false notification about a security improvement is possible. Monitoring makes confirmation scans, but you can also compare several reports from different dates by yourself to verify the vulnerabilities.
- If you are going to make significant changes to your website such as migration or website engine change, we suggest pausing the vulnerability monitoring, at least a day beforehand, using your dashboard. After the changes are finished, resume the monitoring.
Start Security Scanning or Monitoring of your Website.
Who we are, what we do and what we offer.